CSSCurrent en:Logging
General
Cryptshare differentiates between two kinds of logs, the System Log and the Transfer Log. The transfer log is a representation of the transfer data which is being stored in the database. The system log is a regular application logging system and logs all system events such as informational messages or system errors. This includes user operations such as uploads and downloads as well. Therefore the system log also contains the same information as the transfer log, however only as a textual log entry. The contents of each log can be seen at the following locations:
- Transfer Log
- Administration Interface → System Status → Log View → Transfer Log
- System Log
- Administration Interface → System Status → Log View → System Log
- In the lower section of the Administration Interface the most recent log entries are listed
- Log Files in the subdirectory 'log' in the Cryptshare Installation Directory
Transfer Log
Logged Content
In general the transfer log keeps all information belonging to a transfer. This includes the following information:
- Transfer Details
- Product used for providing the transfer
- Unique ID for the transfer (Tracking-ID)
- Time and Date when the transfer was provided
- Time and Date when the transfer will expire
- Transfer Content
- Encrypted File Names (File-IDs)
- File Checksums
- File Sizes
- Transfer Options
- Whether files are listed with their original names in email notifications
- Whether the sender will be informed via email after the transfer was provided successfully
- Whether the sender will receive an email notification each time a recipient retrieves one of the files in the transfer
- Sender Information
- Email address of the sender
- IP Address of the sender
- Recipient Information
- Unique ID per recipient (Transfer-ID)
- Email addresses of recipients
- Download Information
- IP addresses of recipients per download
- Time and Date when files have been viewed or downloaded
Additional Contents
In addition to the contents of a transfer log listed in the chapter above, further content can be kept in the transfer log if the administrator activates the corresponding option.
| Option | Purpose |
|---|---|
| Messages and Subjects | Messages written for the recipient notification are logged including the message subject.
When the message subject is not logged, it does not appear in the transfer logs. However, please be aware that the message and subject are still stored in the database. If logging of messages and subjects is not activated, this data will be deleted from the database once the transfer expires or a request for personal data removal is made. |
| Filenames | The original file names will be logged. If the checkbox is not selected only the encrypted file names will be logged. |
| Zip Content |
The content of zip files will be logged. Please note that zip content will only be logged if the setting 'Log Filenames' has also been enabled. |
Automated deletion of expired log entries
By default Cryptshare keeps all transfer data in the database including the data of expired transfers. If an administrator wishes to delete transfer information of expired transfers after a certain amount of time this option needs to be activated. When active an additional input field allows to setup the interval after which expired transfer data will be deleted from the database.
Sending log data to the administrator
The Cryptshare Server can send a log export to the administrators on a regular basis. This feature is disabled by default.
Interval
The interval of when the log data is sent, can be changed from a minimum interval of one hour up to 2160 hours (90 days).
Covered Period
The period which will be covered by the log export can be changed to two different settings:
- Time period from the last time the log was sent
- Fix period in days
Usually the export data will be sent via email to the administrator. This however is unsecure as the email content is not encrypted. Enable the checkbox to send the data as Cryptshare Transfer if you want to receive a Cryptshare Transfer instead. In this case the data can be retrieved like a usual Cryptshare Transfer with the specified password.
System Log
Use this configuration page to change the settings for the logging of system events. Cryptshare uses the software library LogBack to output general system information. LogBack is configured using an XML file, which can be edited below. By default, information is logged simultaneously to the standard output (console) and to the files 'cryptshare.log' and 'cryptshare\_error.log'. On a daily basis, or by exceeding the maximum size of 50MB, they are stored as ZIP archive and a new, empty log file is created (log rotation). The number and the total size of all archive files is limited. If neccessary, the oldest archives are deleted. The following sections describe the basic elements and configurations - more details can be found in the LogBack manual.
General configuration file structure
Basically, the logback configuration file consists of two types of elements: Appenders and Loggers. Appenders are log output channels, they define where logged information is written to - for example to the console output window or a file. Logger elements allow to specify, per application module, the level of detail which will be used for logging.
Configured Appenders
The default configuration defines three different appenders to handle log information:
- CONSOLE\_DEFAULT - Output to the console window (standard out)
- FILE\_DEFAULT - Logging of all information using the file 'cryptshare.log', excluding stacktraces.
- FILE\_ERROR - Logging of all information using the file 'cryptshare\_error.log', including stacktraces.
There are a number of other possible appenders for LogBack. Please see the corresponding section of the LogBack manual for more information.
Changing the log level
The log level can be defined in five stages:
- trace - Information about the internal program flow
- debug - Detailed information for error analysis
- info - Common information
- warn - Warnings
- error - Errors
Each of the log levels includes outputs of the 'heavier' log level. In log level 'info', for example, warnings and errors are also logged. The log level can be specified generally or, if needed, by application module. The general setting can be defined by configuring the so called root logger:
<root level="error">
This general setting can be overriden by specific Loggers, which specify the package name. For example, log messages coming from Cryptshare Server are logged with detail level 'info':
<logger name="com.cryptshare"
level="info" />
Adjusting the log archiving
Both Appenders FILE\_DEFAULT and FILE\_ERROR (see above) are configured to use an automatic archiving with rotation. After a time interval, or after exceeding a certain size limit, the currently active log file 'cryptshare.log' or 'cryptshare\_error.log' is moved and stored as ZIP archive. Afterwards, the log file will be created again. The time interval can be configured using the 'interval' element. Possible values are: year, month, day or hour. For example, the configuration
<interval>day</interval> <maxFileSize>50MB</maxFileSize>
specifies that a new log file is created every new day or be exceeding 50MB, whichever occurs first. Additionally it can be specified under which confitions old archives are removed. The element 'maxHistory' specifies the amount, 'totalSizeCap' the maximum total size of all archives. For example:
<maxHistory>10</maxHistory> <totalSizeCap>10MB</totalSizeCap>
Regardless of these settings, at least one archive will be kept.
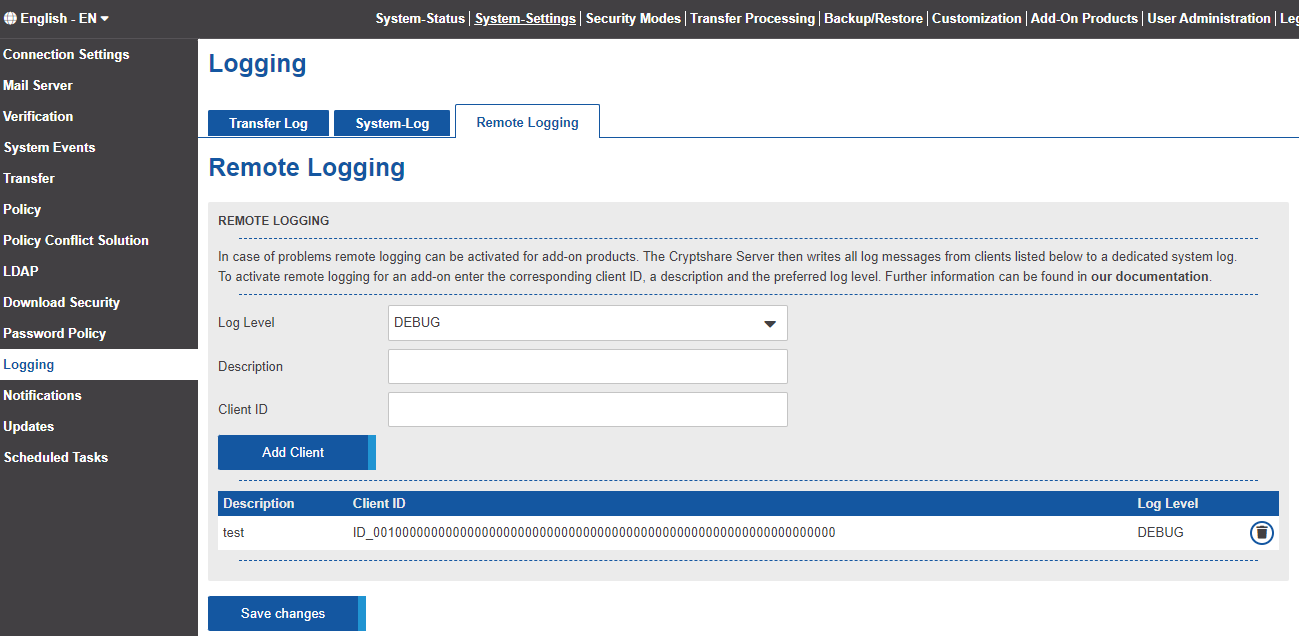
Remote Logging
The Cryptshare for OWA add-in writes logging information into the JavaScript console of the browser. Considering the likely high amount of users/clients working with the add-in, error analysis can get very time-consuming and complicated this way. In order to make this process easier for administrators and users, the add-in is equipped with a so called remote logging feature. This allows administrators to receive logging information from clients at a central place, the Cryptshare Server.
Activate remote logging
In case of problems remote logging can be activated for Cryptshare for OWA add-ins. The Cryptshare Server then writes all log messages from clients to a dedicated system log. There are 5 different log-levels, Info, Warning, Error, Debug and Trace. To activate remote logging for an add-in enter the corresponding client ID, a description and the preferred log level.
- Log-In as an Administrator to the Cryptshare-Server
- Navigate to the upper right column 'System-Settings', then to the left column 'Log Settings' and finally to the 'Remote Logging' section.
- Choose a corresponding Log-Level
- Enter the Description
- Enter the Client-ID
- Press 'Add Client'
- Click on 'Save changes'