CSSCurrent en:LDAP
If the users within your network are managed through an LDAP Server such as Microsoft Active Directory, it is possible to use LDAP groups and users to define the senders and recipients in Policy Rules (see Policy Settings).
The LDAP Server configuration consists of two steps. The first step is for establishing the connection to the LDAP Server. The second step tells the Cryptshare Server which LDAP attributes contain the email addresses of individual users. This step is only available if the LDAP connection is successfully established and settings have been saved.
Step 1: LDAP Server Connection
Depending on what type of LDAP Server you are using, you'll first have to select the LDAP Server type. Currently there are three supported types:
| Server Type | Group Objectclass | User Objectclass |
|---|---|---|
| Microsoft AD | group | person |
| IBM Domino | dominoGroup | dominoPerson |
| OpenLDAP | groupOfNames | inetOrgPerson |
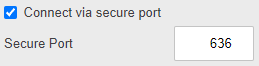
Continue by configuring the remaining connection settings. Depending on how your LDAP Server is set up you may be required to use the secure connection setting:
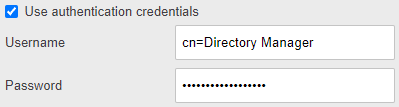
You may also be required to provide 'Bind DN' credentials (User credentials) in order to be able to connect to your LDAP Server. Enter the Username (the NETBIOS/Windows Server 2012 variant) and the password of a User, who is allowed to ask LDAP:
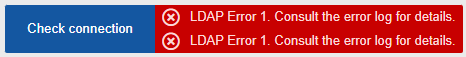
Use the 'Check Connection' button to find out whether your settings are correct and if a connection can be established. If no connection can be established, a respective error message will appear. Along with the error message a more detailed log entry will give more precise information about this error together with an LDAP 'ResultCode'. The result code is a standardized LDAP result code. For more information on single LDAP result codes please refer to the following links:
- http://tools.ietf.org/html/rfc4511#appendix-A
- https://www.unboundid.com/products/ldapsdk/docs/javadoc/com/unboundid/ldap/sdk/ResultCode.html
Step 2: LDAP Attribute Selection
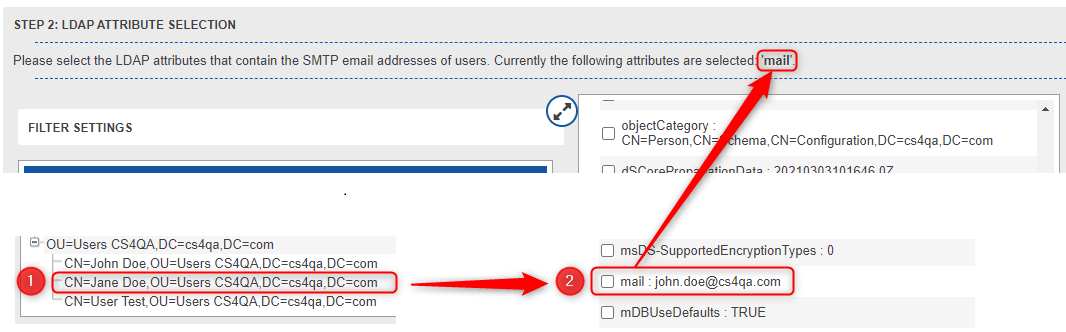
After successfully configuring the LDAP connection settings, section 2 for the LDAP settings will appear and offer a visual interface for selecting the LDAP Attributes containing the email addresses of individual LDAP users.
On the left hand side an LDAP Tree containing all LDAP entries is shown. Select a user entry by clicking on it. While hovering with the mouse above single entries, a popup will occur showing the LDAP attribute values for this entry:
When selecting an entry, an additional view will appear on the right side showing the LDAP attribute names and corresponding values. If you have selected an LDAP user entry, you can now go on and select those LDAP entries containing the email addresses of users.
Finish the configuration by clicking the 'Save' button. Cryptshare is now ready for setting up LDAP-based Policy Rules (see Policy Settings).