CKB:SSL certificates
Applies to
Purpose
In this article, you will find an overview on how to set up a new SSL certificate, install your wildcard certificate, generate a CSR or resolve certificate related error messages.
Solution
Generating CSR from existing keystore
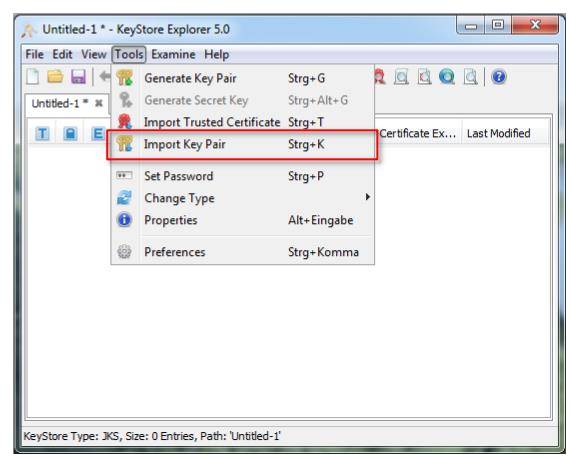
If you already have a Keystore on your Cryptshare Server and would like to generate a CSR (Certificate Signing Request) for a certificate authority please follow this article:
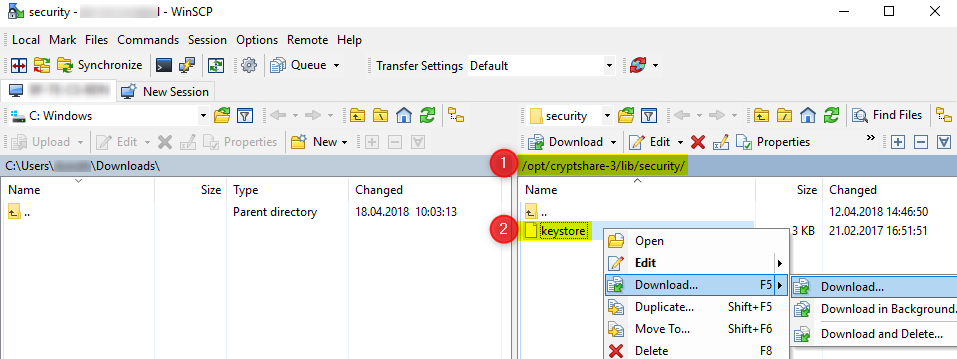
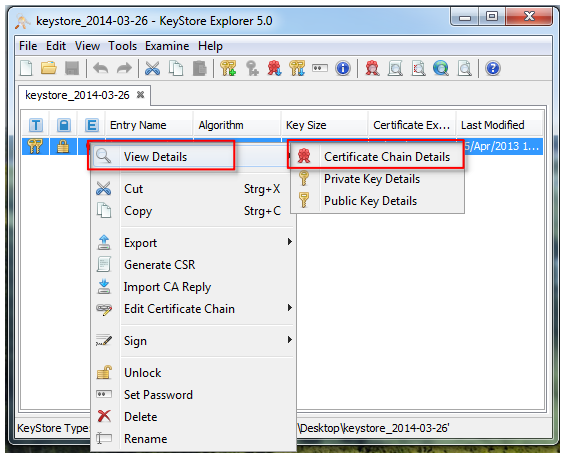
1. copy current KeyStore from your Cryptshare Server to your computer by using WinSCP
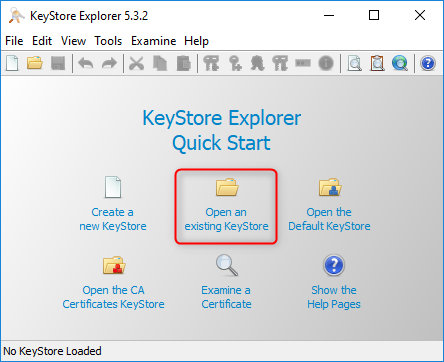
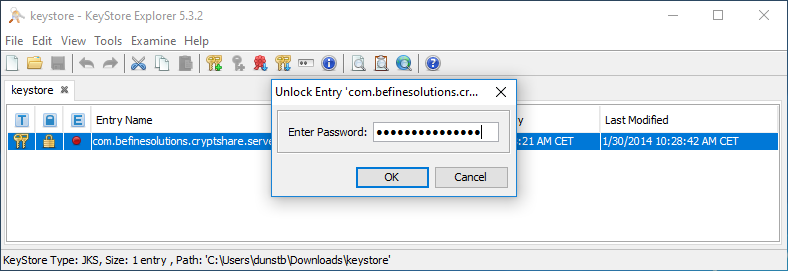
2. open the KeyStore with KeyStore Explorer
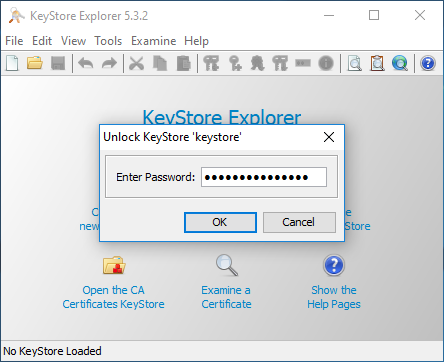
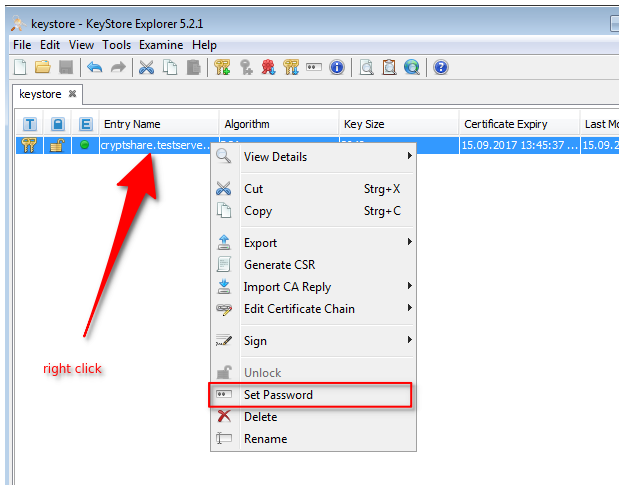
3. enter the password 'CA0AZhuFM4NogQh'
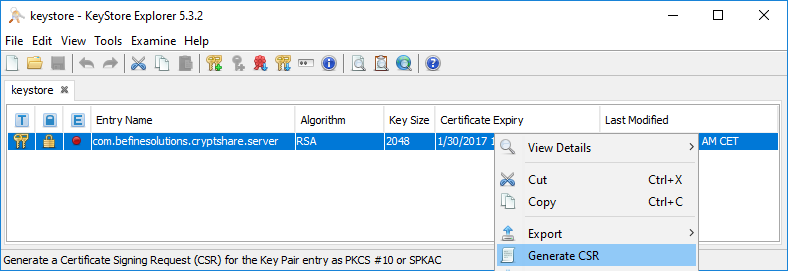
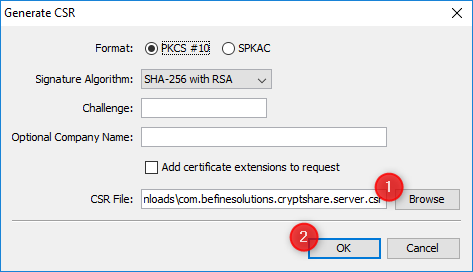
4. generate CSR
5. enter the password 'CA0AZhuFM4NogQh' again
6. save the CSR File
7. please proceed with the paragraph Public SSL Certificate
Installation of an existing SSL certificate (e.g. wildcard SSL certificate)
This article describes how to install an already existing SSL certificate (e.g. wildcard SSL certificate) to your Cryptshare Server
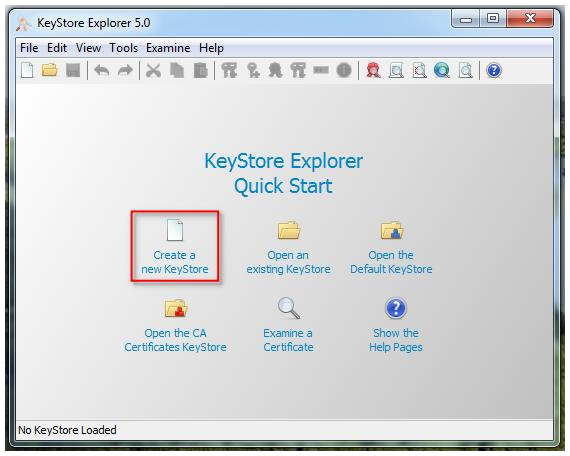
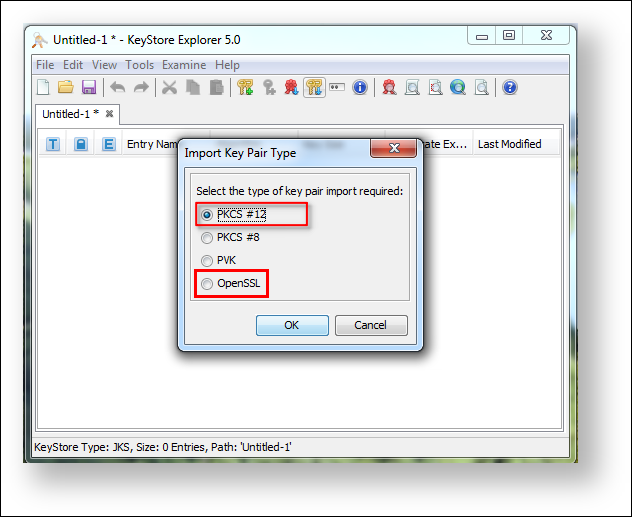
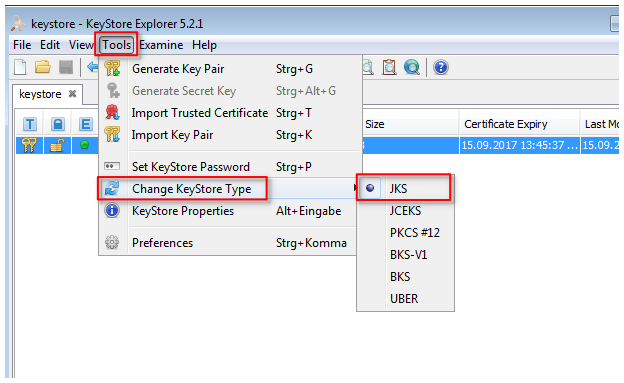
- Create new Java-Keystore with KeyStore Explorer
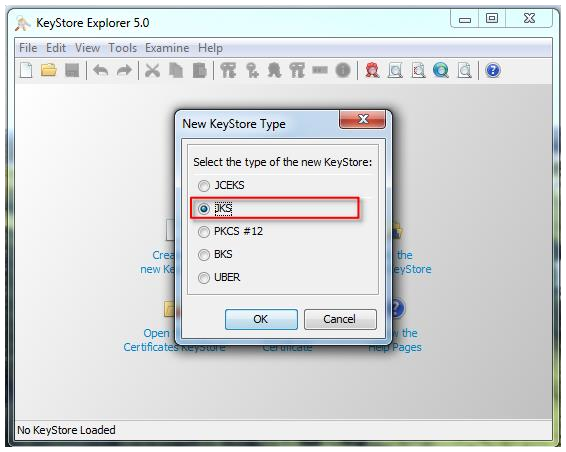
2. Select JKS for new KeyStore type
3. Import the available SSL certificate
4. Select the certificate format, e.g. pkcs12 (.pfx) or OpenSSL (.crt, .cer, .pem)
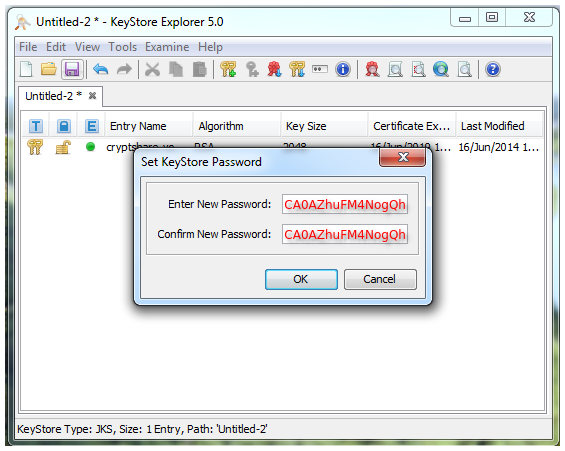
5. Use the default password 'CA0AZhuFM4NogQh', to import the key pair
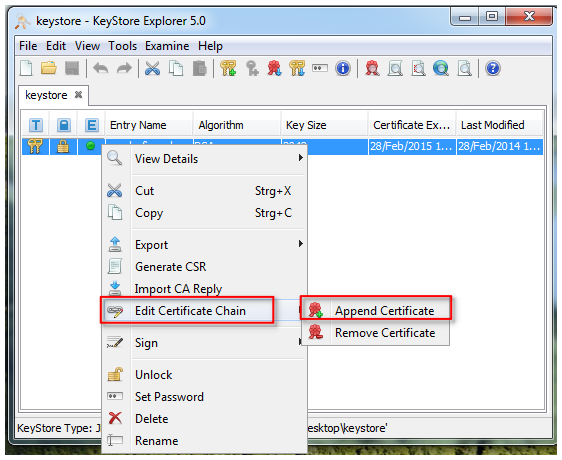
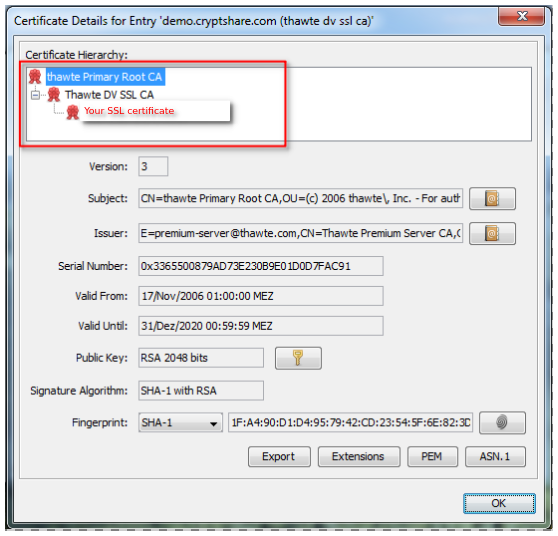
6. Import and check the certificate chain
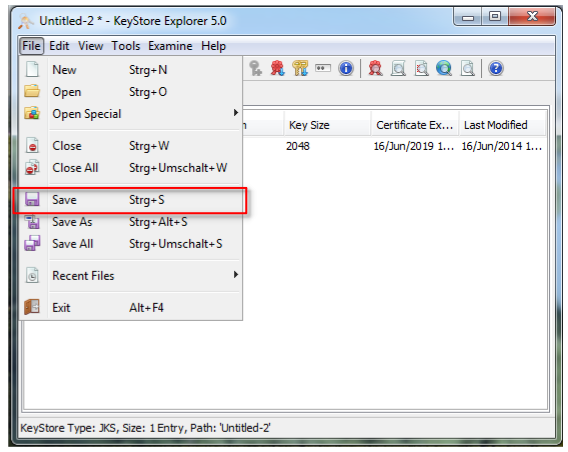
7. Save the KeyStore
8. Use the default password 'CA0AZhuFM4NogQh', to save the KeyStore
9. Install the created KeyStore on the Cryptshare Server Setting up an SSL Certificate
Start failed after SSL KeyStore installation
A new KeyStore is created or a new SSL certificate is installed in the existing KeyStore, but the Cryptshare Server start failed after the KeyStore is installed.
The most common reason is a wrong KeyStore format or a wrong password. Please check whether the following settings are correct:
- The format of the KeyStore is 'JKS'
2. the password for the certificate in the KeyStore is the default password 'CA0AZhuFM4NogQh'
3. The password for the KeyStore is the default password 'CA0AZhuFM4NogQh'
The requested public SSL certificate cannot be imported
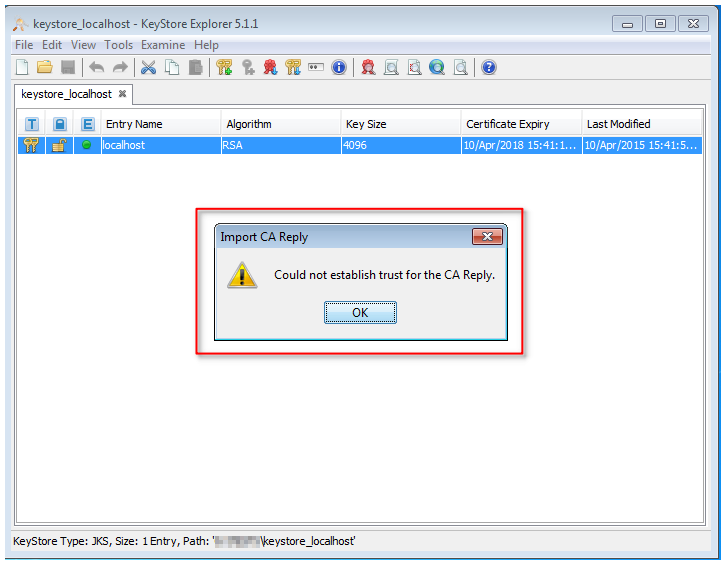
The requested SSL certificate cannot be imported into the Keystore with the following error:
- English: Could not establish trust for the CA Reply.
- German: Vertrauenskette für die CA Antwort konnte nicht erstellt werden.
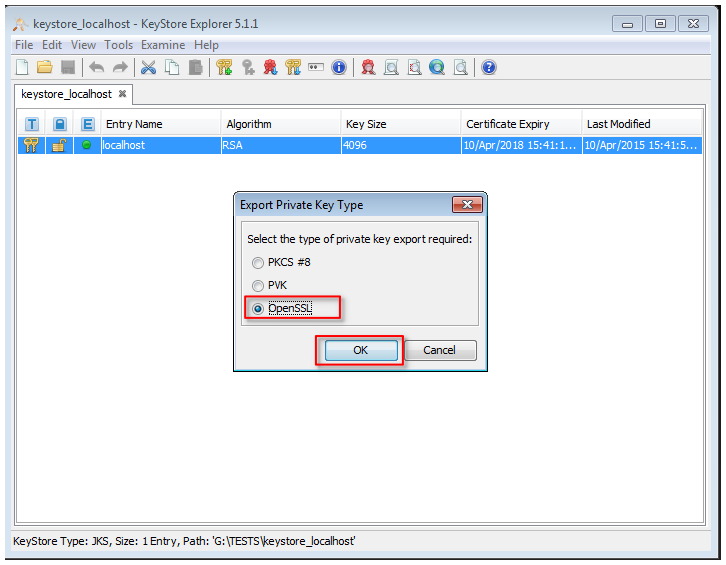
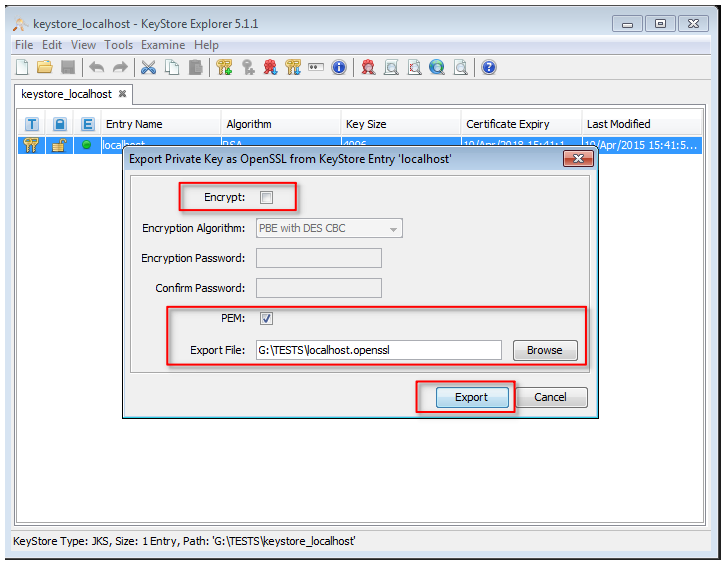
Export the private key from the keystore used for the creation of the CSR file and import it together with the requested SSL certificate into a new keystore.
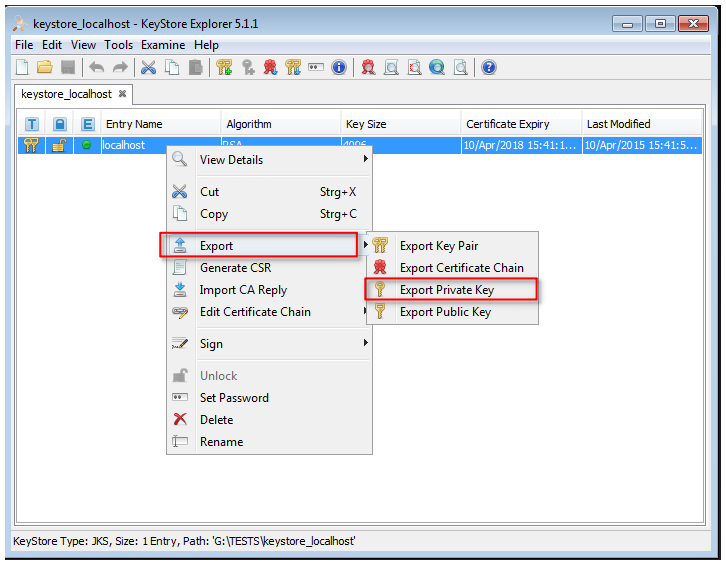
1. open the existing keystore used for the generating of the CSR file
2. klick with the right mouse button on the entry in the keystore
3. open the menu entry 'Export --> Export Private Key'
4. save the private key in OpenSSL format to your local machine
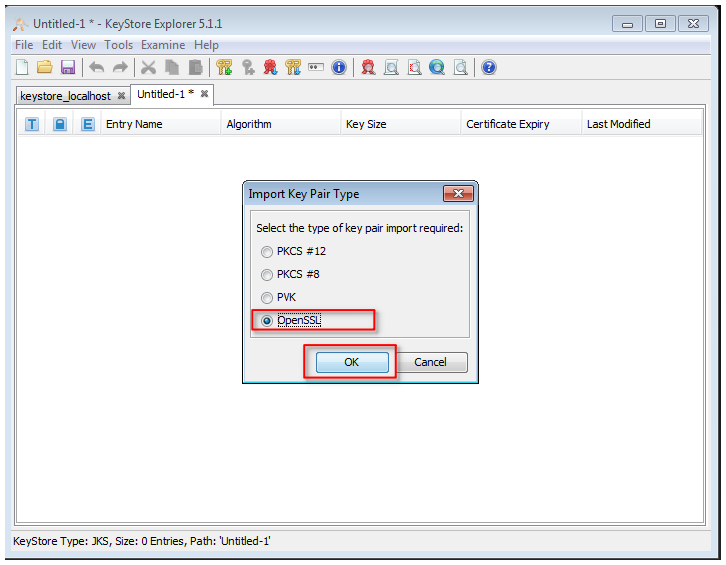
5. create new Java-Keystore of type JKS
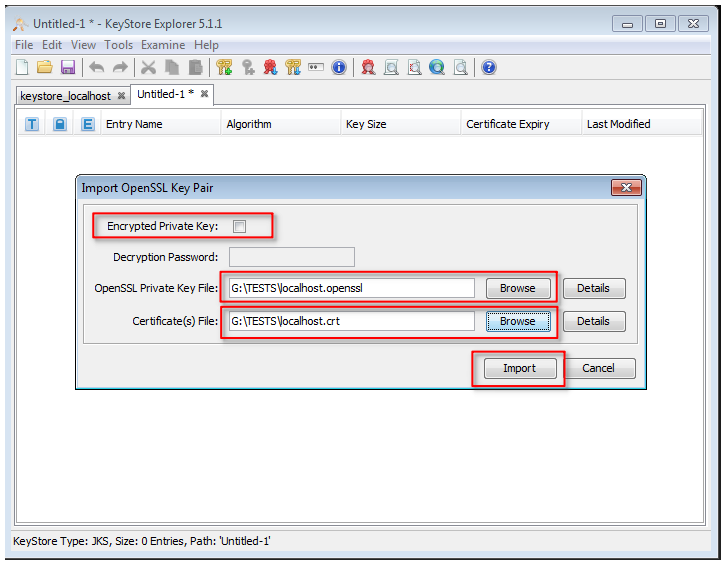
6. impot the available SSL certificate
7. select the certificate format, e.g. pkcs12 (.pfx) or OpenSSL (.crt, .cer, .pem)
8. import and check the certificate chain
9. save the Keystore
10. use the default password 'CA0AZhuFM4NogQh', to save the Keystore
11. install the created keystore on the Cryptshare server Setting up an SSL Certificate
The connection to LDAP cannot be established using SecureLDAP
If the connection to LDAP cannot be established using SecureLDAP, the cause is usually that a self-signed SSL certificate is installed on LDAP server, which cannot be trusted by Java.
Follow the steps below in order to import the LDAP SSL certificate to Java keystore of Cryptshare Installation:
Linux Server
- copy the SSL certificate in x.509 format (.cer, .crt, .pem) to the folder /root
- log in as root on the appliance
- change into Java folder and change the permissions for keytool
| `cd` `/opt/cryptshare-3/jre/bin/`
`chmod` `+x keytool` |
- import the SSL certificate
| `.``/keytool` `-``import` `-trustcacerts -keystore ..``/lib/security/cacerts` `-``alias` `<sitename> -``file` `<SSL Certificate>` |
where <alias> is the name of LDAP server and <SSL Certificate> is the certificate inclusive the path, e.g. /root/LDAP-SSL-certificate.crt The default password for the JAVA certificate storage is changeit
- restart Cryptshare service
| systemctl restart cryptshare (use rccryptshare restart up to and including v.7.1) |
Windows Server
- copy the SSL certificate in x.509 format (.cer, .crt, .pem) to the server
- open command line
- change into Cryptshare Java folder
| `cd` `<Cryptshare installation folder>\jre\bin` |
- import the SSL certificate
| `keytool.exe -``import` `-trustcacerts -keystore ..\lib\security\cacerts -``alias` `<sitename> -``file` `<SSL Certificate>` |
where <alias> is the name of LDAP server and <SSL Certificate> is the certificate inclusive the path, e.g. <User Desktop>\LDAP-SSL-certificate.crt The default password for the JAVA certificate storage is changeit
- restart Cryptshare service
Now the SecureLDAP connection should work fine.