CSRCurrent en:SSL Certificate Installation
SSL Certificate Installation
If the Cryptshare Server uses a self-signed certificate or a certificate that is signed by a certificate authority which is not automatically trusted by the Robot's Java Runtime, you will not be able to establish a secure connection to the Cryptshare Server, and so the Cryptshare Robot will not be able to function properly. If you receive SSL Connection errors when trying to run the Robot application, you can add the Crypthare Server Certificate as a trusted certificate to your Java Keystore with the free Keystore Explorer Tool as described below.
Keystore Explorer
The free Keystore Explorer can be downloaded at the following URL: https://keystore-explorer.org/downloads.html The tool can be used for all management operations for a Java SSL certificate. This applies to certificates on Windows systems as well as on Linux systems.
- Start Keystore Explorer with administrative permissions:
- Click on 'Start'
- Find the shortcut 'Keystore Explorer x.x.x'
- Right click on this entry
- Select 'Start as administrator' in the menu
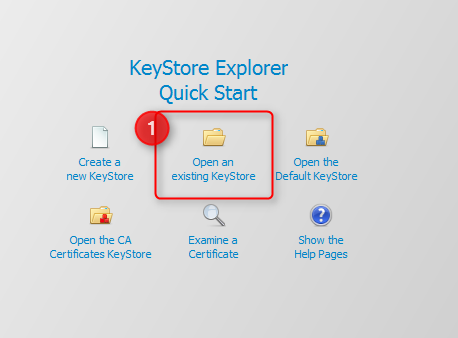
If you do not have the Cryptshare Server certificate file available, you can export it from the Cryptshare Server's key store using the Keystore Explorer. If you already have the "*.cer" certificate file ready, you can skip this section and continue on to the next section Install the Cryptshare Server Certificate in the Client's Java Runtime. If you have a GUI available on the Cryptshare Server machine, you can run the Keystore Explorer application directly on the server machine, otherwise simply copy the keystore file from the Cryptshare Server to your working computer, so you can open the file with the Keystore Explorer. The Cryptshare Server keystore file is located at path-to-server-installation-directory/lib/security/keystore. On the Keystore Explorer Start Screen, select "Open an existing KeyStore" and select the Cryptshare Server keystore file from the file selector popup window.
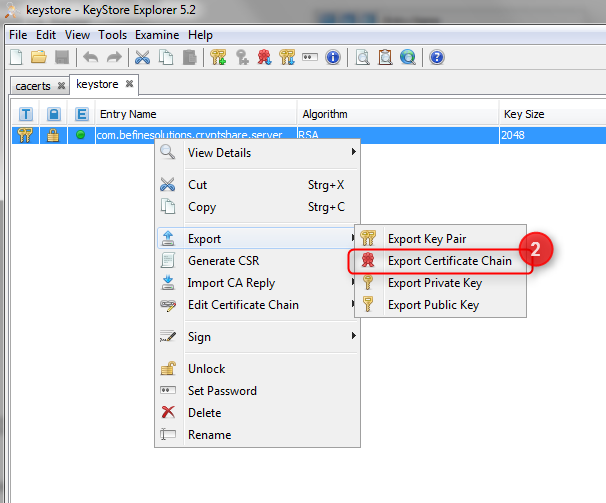
The Keystore Explorer then prompts you for a password to access the keystore file. The default password for the keystore of a new Cryptshare Server Installation is 'CA0AZhuFM4NogQh'. However, your server administrator may have changed the password. See Web Server Configuration - SSLConfiguration. Once the keystore file is open in the Keystore Explorer, you can see the Cryptshare Server certificate in the list. Right-click on the entry and choose "Export->Export Certificate Chain" from the popup menu:
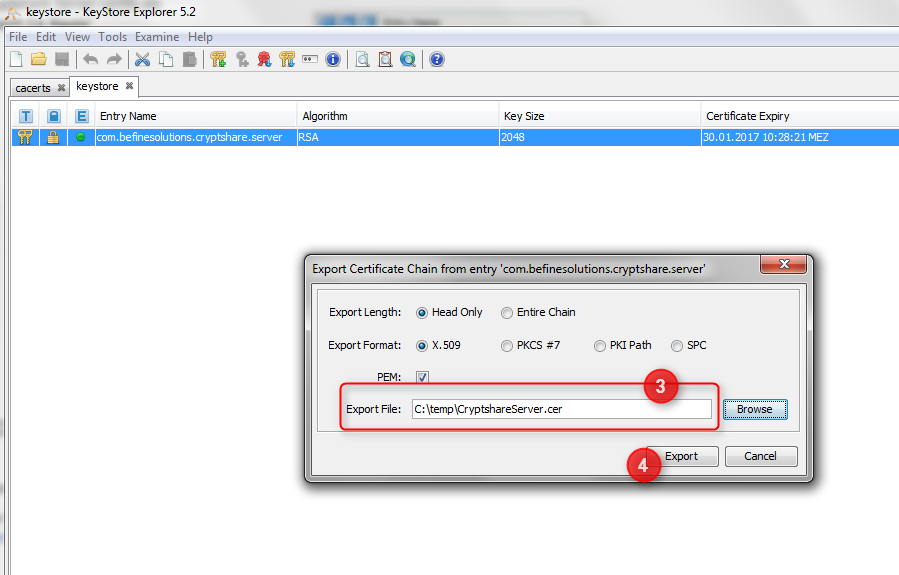
This will open the export settings dialog. You can leave the standard settings unchanged, and just choose a file name and location under which to save your exported certificate file. Then click "Export".
The exported server certificate file can now be imported to the client's Java Runtime Certificate Store, as described in the next section.
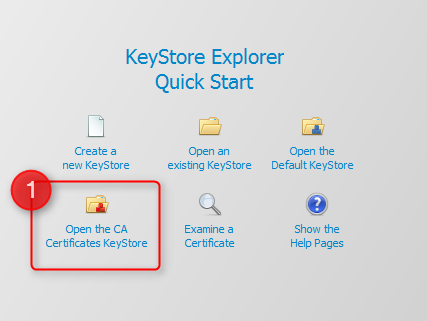
You can now use the Keystore Explorer to install your Cryptshare Server Certificate to the Java Runtime's Keystore. Make sure you start the Keystore Explorer with administrative permissions, so that you have write access to the Java Keystore, or you will not be able to save any changes. On the Start Screen of the Keystore Explorer, click on the option "Open the CA Certificates KeyStore", which will automatically open your Java Runtime's certificate key store file, which is located at path-to-jre/lib/security/cacerts.
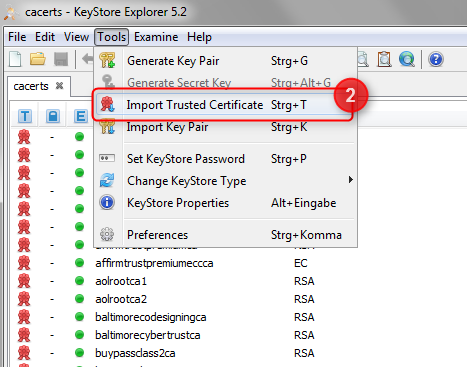
To install your Cryptshare Server certificate file, select "Import Trusted Certificate" from the "Tools" menu, and then select your Cryptshare Server's certificate file from the file selector popup window.
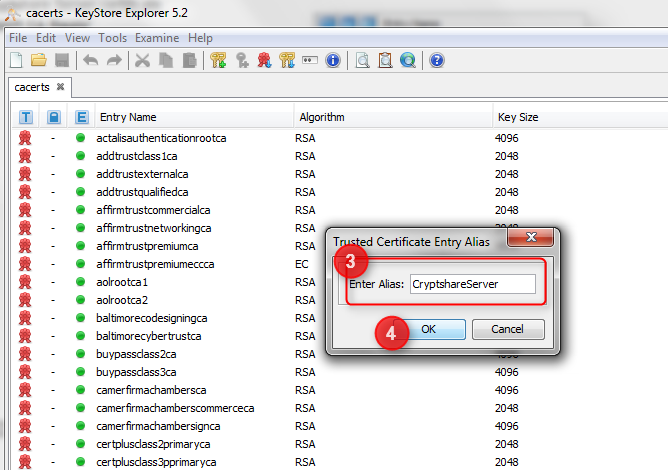
The Keystore Explorer then prompts you to enter an Alias for the certificate file. This will be the name under which the certificate will be stored in the certificate store. Enter a name and click OK.
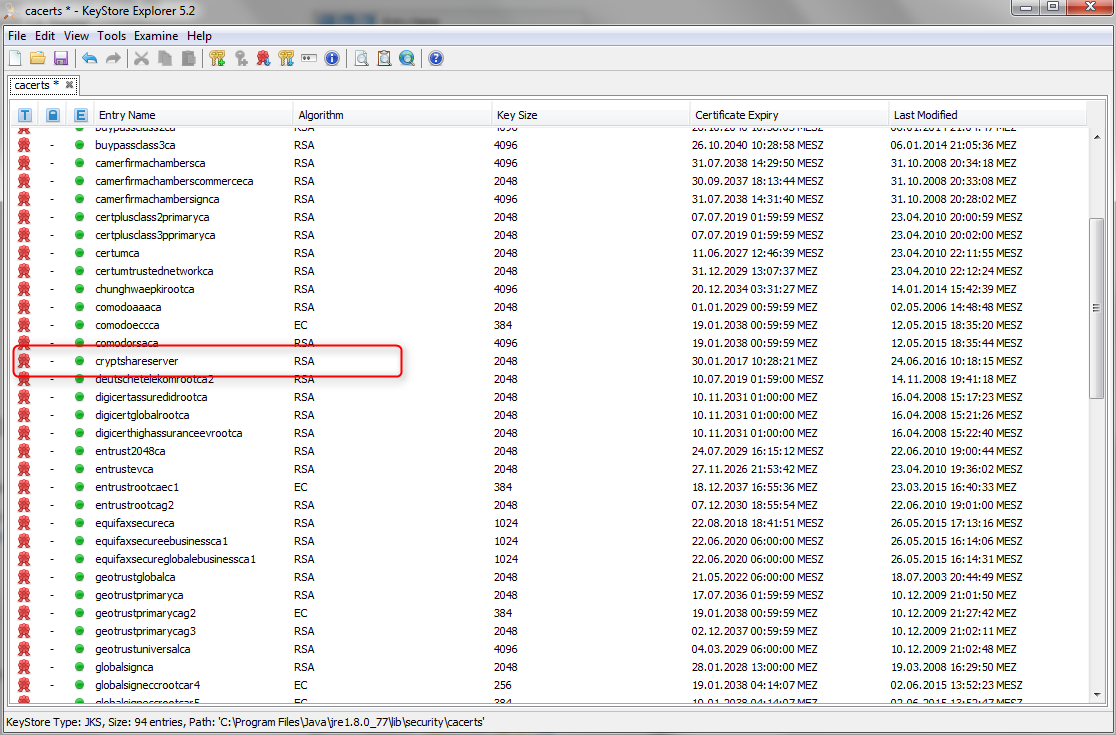
The Cryptshare server certificate will now be available in the Java Runtime's Certificate Store:
Don't forget to save the certificate store. When the Robot is now started, it will be able to create a secure SSL connection to the Cryptshare Server, since the Java Runtime now knows and trusts the Cryptshare Server certificate.